


Protect Networks and Devices
Attack Surfaces and Losses are Growing Exponentially
Detecting and responding to cyber-intruders used to be manageable, things have changed. Remote working, IoT device proliferation, and a host of other forces have reshaped the attack surface landscape. Hackers rake in $200 billion dollars more per year than the global illegal drug trade exploiting the vulnerabilities they find. Our autonomous solution is designed to be more aware, more automatic, and more adaptable to this new reality.
75
Per Second are Stolen by Hackers
$4.2
Average Breech Cost
$10
in Expected Annual Losses by 2025

Distributed Network Solutions
Automatically Detect and Protect Against Emerging Security Risks
Providing Services For
Finance
Providing Services For
Healthcare
Providing Services For
Law
Providing Services For
Education
Providing Services For
Government
Providing Services For
Small Business
Securing Edge Territory

Autonomous Detection and Response
Hackers Rarely Take a Break, We Never Do
The average hacker can break into a vulnerable network in a few minutes, we stop attacks in milliseconds. Regular scans are made of your network and devices to automatically stop threats and to find vulnerabilities that can be fixed before they are exploited by hackers. With our distributed version, you can protect multiple locations, remote employees, and more.
Distributed Enterprise Version
Autonomous Detection and Response for the Global Enterprise
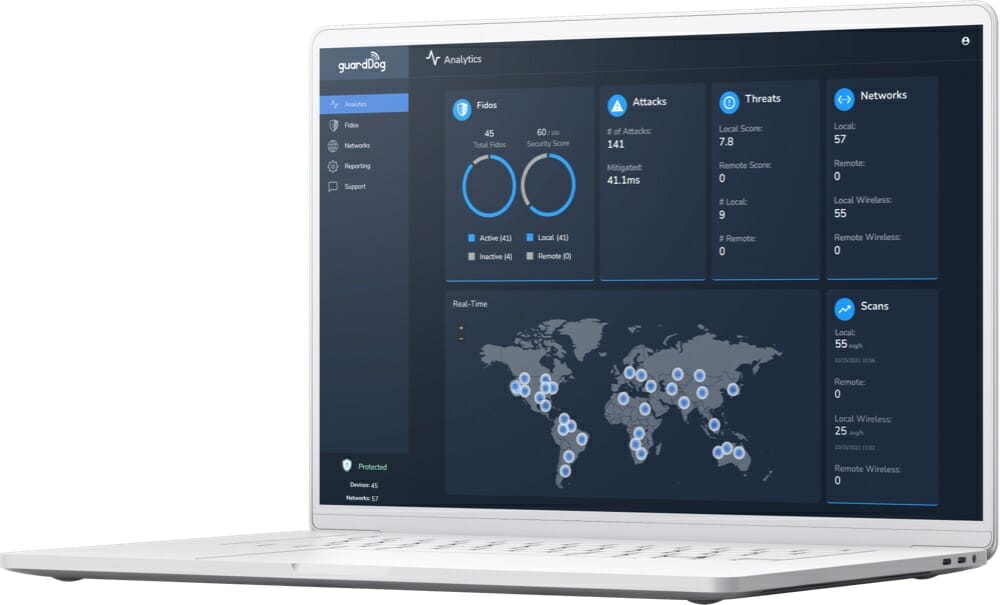
Our cloud-based dashboard for makes it easy to deploy and manage many site locations. Threats are recognized and terminated immediately. Vulnerabilities are scanned for constantly. Insights into networks and attached devices are readily at hand. Our autonomous incident response (AiR) technology provides an intelligent response to known threats, interprets new attack patterns, and gets smarter over time with artificial intelligence. We are out to make cybersecurity defense more automatic.
- Detects and responds to threats automatically
- Manages many deployed sites
- Ranks and scores threat and vulnerability incidents
- Matches detected incidents to CVE databases
- Produces threat score to manage security hygiene
- Generates detailed logs and analytics
- Performs regular vulnerability scans
- Maintains site specific privacy settings
- Compliments existing security investments
- Enterprise integration services available
- Optional support programs available
Get Started Today
Recieve your exclusive access via email. Please submit your request for access today!