Peter Bookman
Founder & CEO at Guard Dog Solutions
So, what is edge territory?
Edge territory is a new term born out of necessity to describe a new space created by the evolving security environment that networks and devices coexist in. Our understanding of this new term starts where prior terms leave off. The term most relevant to this context is the ‘network edge.’ While there are many definitions for network edge to be found, I thought this one summed it up nicely:
Network Edge – The point at which the enterprise-owned network connects to a third-party network is known as the network edge.
The term network edge conjures thoughts of a cliff edge and implies that what lies beyond it were an empty void. Or perhaps another visualization would be like minding the gap when stepping between a platform and a train car. In reality, this seemingly small space is an invisible and vast territory between environments. It’s a wild-wild-west no-man’s land where secured private networks, unsecured public networks, IoT devices and more mingle in an unregulated, unmonitored, and unseen threat opportunity zone.
What looks like a small gap can be deceiving. And what is invisible can be quite large. For the Harry Potter fans out there, edge territory is the proverbial Platform 9 ¾ of network security, where most people can’t see the entrance and have no idea of the scope of what’s going on inside.
Such a reality requires a new vocabulary for discussion, so that solutions can emerge that combat threats and secure travel through this territory, so to speak. Here is the working definition for this new edge territory term:
Edge Territory – The unmapped space beyond the network edge that exists between environments, where secured and unsecured networks and devices collide, known as edge territory.
Edge territory seeks to define these invisible spaces where edge devices (and IoT) exist, creating new definitions, new understandings, and new cybersecurity strategies as a result. From a security perspective, this is particularly important because if you cannot see it, you cannot protect against it. Conversely, if you can see it, you can protect against it.
Much like the area between planets and bodies in outer space, edge territory is expansive and borders everything. It touches every network and every device. A simple digital doorbell, a video camera, a smart refrigerator, or any other IoT device connected to a network can introduce pathways to be exploited, all of which border edge territory.
Consider the mobile smartphone and the average person. How often does a smartphone automatically connect with unknown but open public wi-fi networks? Do they automatically think to themselves, “Oh cool, free wi-fi!” Unfortunately, this isn’t a consequence free environment, free has a cost. After all, the level of security that exists on a network, public or private, and who else is on that network is generally not known by the average person. This lack of expertise and the access to the right tools leaves them vulnerable and can create the conditions where they inadvertently undermine their own security.
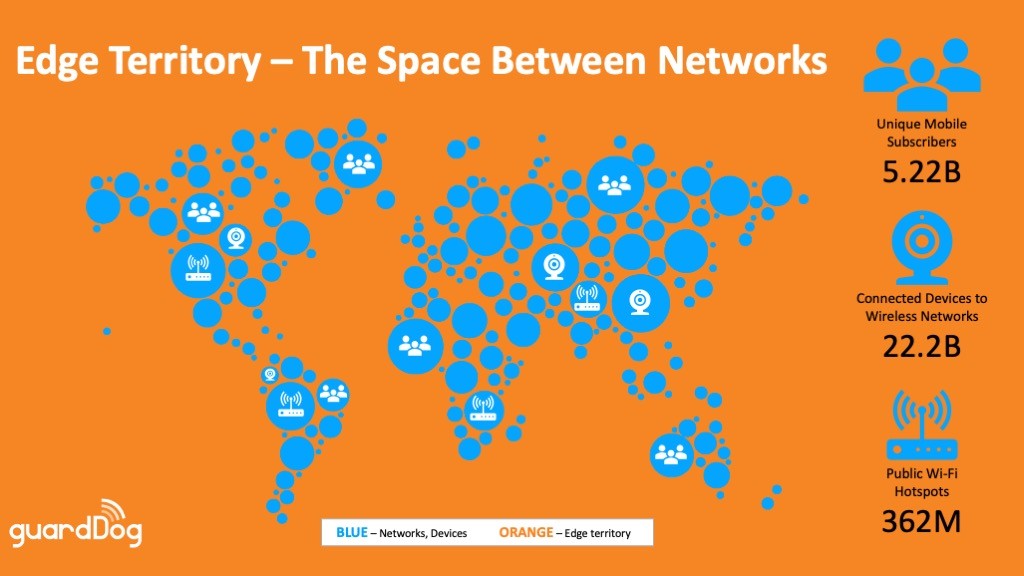 As the saying goes, you are only as strong as your weakest link. As shown in the chart above, billions of people on devices and networks are actively traversing edge territory globally, and often have no idea if something happened while they were there. No person, business, government, or any other entity is immune from potential losses which can be devastating to the tune of trillions of dollars annually.
As the saying goes, you are only as strong as your weakest link. As shown in the chart above, billions of people on devices and networks are actively traversing edge territory globally, and often have no idea if something happened while they were there. No person, business, government, or any other entity is immune from potential losses which can be devastating to the tune of trillions of dollars annually.
Tales from edge territory
So, what kind of nefarious things are going on in edge territory? Here are couple of stories about what happens in this invisible space.
Workers robbed while working remote
The places where we work from are changing. We are working from home. We are working from cafés. We are working from hotels. This trend has been accelerated by a global pandemic, and those that would prey on these workers have taken notice. Access to sensitive work information, including personal information, are at greater and ever-growing risk. Small or remote offices also lack the expertise or the tools to protect themselves in these high-risk edge territory border zones. People with personal and corporate issued devices hop from network to network circumventing protections and introducing new vulnerabilities, usually unknowingly.
One example of attacks lying in wait in hospitality environments is a sophisticated attack known as ‘DarkHotel.’ From this threat analysis by Kaspersky Lab: DarkHotel uses highly sophisticated techniques at high-end hotels, to ensnare top executives across industries in what is known as a ‘spear-fishing attack’ aimed at stealing sensitive data. One attack example cited was a Flash vulnerability that prompts the victim to install a software update before continuing, which then introduces malware when installed.
The bottom line here, is by simply joining the guest network of a hotel, our safeguarded devices and information on them can be compromised.
Predators hack video devices in the home
Another alarming tale from edge territory happened last year when someone broke into a family’s wi-fi security camera and told an 8-year-old child they were Santa Claus. While the manufacturer claimed it was likely loose password management that caused the intrusion, the truth is often people just don’t know how it happened. There is nothing that really monitors for these sorts of vulnerabilities and activities, so therefore they are often discovered after the fact, assessed long after the damage has been done (in many cases, months afterwards).
Also mentioned in the article was a father sharing a story of how he was shocked to overhear a voice talking to his daughter on their kitchen counter through their video device, and another story where a woman reported being woke from sleeping by a man yelling at her and demanding she wake up!
Needless to say, these and many other situations where the digital world remains invisible until attacks take place always bring with them very similar vulnerabilities as physical break-ins, and often with similar trauma for those being victimized.
Cutting edge territory
My entire career has been in cybersecurity technology, and even I have clicked on the wrong link from time to time and have occasionally roamed onto free wi-fi without a second thought (and I’m an expert!). Still, I’m more security conscious than most. But for the masses I would ask who among us is a cybersecurity professional? Most people don’t understand security beyond a password, and even professionally managed security networks can be undermined unintentionally as the unknowing masses move deeper into edge territory. For enterprise networks, even VPNs are not enough. Having 24/7 visibility and the resources to respond is expensive, complicated, and incomplete to address the changing landscape.
I am excited to announce that the company I founded and helm as CEO, guardDog, is offering the first comprehensive approach to map edge territory. guardDog provides visibility and awareness into the threats that lurk there and protects those that travel through it. guardDog is a combination of device, cloud service, and AI threat mitigation technology that work together in concert to identify and address threats in this new domain.
Like a family dog that knows who you are and senses threats before you do to protect you, guardDog offers a cybersecurity solution that cost-effectively secures everything from a small-scale home network to a large-scale distributed enterprise. guardDog protects the digital you when you go for a walk in edge territory.
Trillions of reasons to secure edge territory
Despite over 20,000 existing software options available for cybersecurity, as well as a predicted spending of $1 trillion dollars on global cybersecurity over 5 years, the world STILL expects to lose $10.5 TRILLION ANNUALLY by 2025!
Clearly new understandings and approaches are needed. Gaining visibility and autonomous protection in edge territory is one possible answer to the following perplexing question:
Why have increasing cybersecurity investments been inadequate to keep pace with and mitigate the explosion of losses from breaches?
If you cannot see it and understand it, it is nearly impossible to protect against it. Regardless of where you are in the digital world you are likely bordering edge territory, and good luck is not an adequate security policy. That’s where guardDog is stepping in and defining how to defend this space.
I look forward to continuing to share my thoughts on edge territory. If you have any comments, or perhaps some stories of your own from edge territory, please make a comment below! (p.s. if you want to know more about what I’m up to, check out guardDog.ai)
About guardDog.ai
guardDog.ai provides a software service that simplifies cybersecurity management with AI-powered autonomous detection and response technology. The solution is designed to make advanced cybersecurity accessible for small, mid-market, and distributed organizations without complexity. It can be easily deployed on hardware, in virtualized environments, embedded systems, and more, offering automatic protection at the network level. Hidden threats to networks and devices are made visible and instantly terminated with intelligent countermeasures, and detected vulnerabilities are exposed. Management of the service, incident and severity level reporting, and access to additional advanced features are accessed through a cloud-based security operations dashboard. For more information, please email dealers@guardDog.ai or visit the guardDog.ai dealer page here.
Contacts
Sales Contact:
sales@guarddog.ai
833-248-2733