Our solution – Simplified Cybersecurity Analytics
Simple deployment in minutes – Not days
Analytics in real time – Not hours
Hundreds of dollars per site per year – Not hundreds of thousands of dollars per site per year
PROTECTIVE CLOUD SERVICE (PCS)
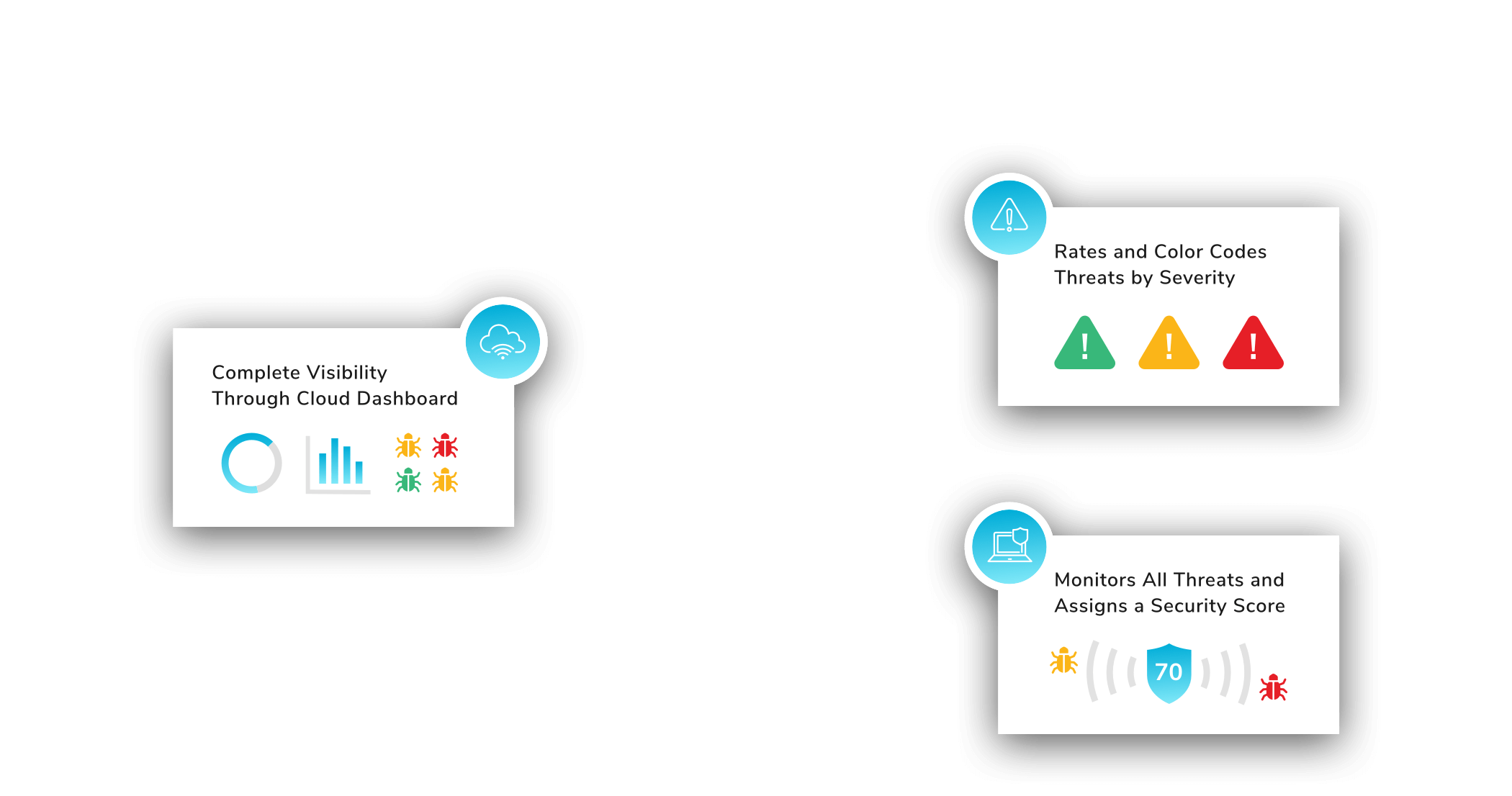
- Gather Information and Analytics
- Near Real-Time analytics and alerts which allows you to take action before critical damage is done to your network
- Stops the attack and gives you time to make adjustments


FIDO
- minutes to install
- protects both wifi and wired networks
- interrupts attempted attacks
VIRTUAL FIDO
- minutes to install
- protects both virtual or cloud networks
- interrupts attempted attacks

Frequently asked questions?
Why choose GuardDog?
You can always know how secure you are on any size network or environment.
How quickly will I recognize I am under attack?
GuardDog will notify you instantaneously and will also interrupt the attack from being successful.
Why are GuardDog analytics so effective?
It’s the only one simple enough to be deployed in any environment regardless of complexity or size. Minimal technical knowledge required to interpret the source of the issue.
How do I manage my score?
With the simplified analytics we provide, IT resources with sufficient knowledge will be able to respond. Our support team is ready to help anyone.
